Difference between revisions of "31 May 2012"
(more links) |
(US+Israel developed Flame, officials say) |
||
| (2 intermediate revisions by the same user not shown) | |||
| Line 9: | Line 9: | ||
'''Updates:''' | '''Updates:''' | ||
| − | *[http://arstechnica.com/security/2012/06/flame-crypto-breakthrough/ Crypto breakthrough shows Flame was designed by world-class scientists] ''- by Dan Goodin - June 7 2012'' | + | *[http://www.washingtonpost.com/world/national-security/us-israel-developed-computer-virus-to-slow-iranian-nuclear-efforts-officials-say/2012/06/19/gJQA6xBPoV_story.html US+Israel developed Flame, officials say] |
| − | *[http://arstechnica.com/security/2012/06/why-antivirus-companies-like-mine-failed-to-catch-flame-and-stuxnet/ Why antivirus companies like mine failed to catch Flame and Stuxnet] ''- F-Secure's Chief Research Officer: A/V outfits were out of their league'' | + | *[http://arstechnica.com/security/2012/06/flame-crypto-breakthrough/ Crypto breakthrough shows Flame was designed by world-class scientists] |
| + | :''- by Dan Goodin - June 7 2012'' | ||
| + | *[http://arstechnica.com/security/2012/06/why-antivirus-companies-like-mine-failed-to-catch-flame-and-stuxnet/ Why antivirus companies like mine failed to catch Flame and Stuxnet] | ||
| + | :''- F-Secure's Chief Research Officer: A/V outfits were out of their league'' | ||
*[http://arstechnica.com/security/2012/06/flames-god-mode-cheat-code-wielded-to-hijack-windows-7-server-2008/ Flame's "god mode cheat code" wielded to hijack Windows 7, Server 2008] | *[http://arstechnica.com/security/2012/06/flames-god-mode-cheat-code-wielded-to-hijack-windows-7-server-2008/ Flame's "god mode cheat code" wielded to hijack Windows 7, Server 2008] | ||
| + | *[http://www.securelist.com/en/blog/208193566/Flame_Replication_via_Windows_Update_MITM_proxy_server Replication via Windows Update MITM proxy server] ''- Aleks, Kaspersky Lab Expert'' | ||
}} | }} | ||
Latest revision as of 03:27, 20 June 2012
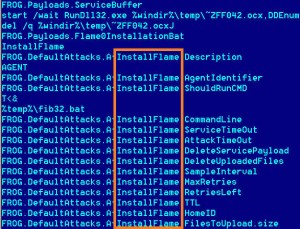
Iran invites malware into their nuclear facilities
After Obama and Israel released the Stuxnet worm to attack Irans nuclear facilities in 2010, another virus being called Flame has now been discovered which does even more damage.
Infiltration of the computer systems in a tightly secured nuclear facility would normally be a practically impossible task, but the US and Israel had an amazing stroke of good luck; they discovered that Iran was using Windows operating systems in its nuclear facilities which are renowned for being the most insecure and vulnerable operating systems currently available!
So once this valuable piece of information was known it was a simple matter of applying a few of the well known Windows exploits, such as putting some malicious code into removable media's autorun.inf files or gaining complete control of a machine via flaws in the graphical user interface programming.
It seems almost like Iran was inviting such an attack - why on earth would such insecure software be used for something so security sensitive? why would they carry on using Windows after being infected by Stuxnet? why are they even supporting US companies with their IT budget? It seems to be about as ridiculous as the death star having a self-destruct button in the middle just waiting for a Jedi to fly in and press it!
Updates:
- US+Israel developed Flame, officials say
- Crypto breakthrough shows Flame was designed by world-class scientists
- - by Dan Goodin - June 7 2012
- - F-Secure's Chief Research Officer: A/V outfits were out of their league
- Flame's "god mode cheat code" wielded to hijack Windows 7, Server 2008
- Replication via Windows Update MITM proxy server - Aleks, Kaspersky Lab Expert