Difference between revisions of "Secure Sockets Layer"
m |
|||
| Line 65: | Line 65: | ||
*[[1 July 2013]] ''- our move over to Nginx'' | *[[1 July 2013]] ''- our move over to Nginx'' | ||
*[[Install a new server]] | *[[Install a new server]] | ||
| + | *[[Security]] | ||
| + | *[[Privacy]] | ||
*[http://www.networkcomputing.com/next-generation-data-center/commentary/servers/many-ssl-connections-missing-added-prote/240157853 Many SSL Connections Missing Added Protection, Netcraft Says] | *[http://www.networkcomputing.com/next-generation-data-center/commentary/servers/many-ssl-connections-missing-added-prote/240157853 Many SSL Connections Missing Added Protection, Netcraft Says] | ||
*[http://news.netcraft.com/archives/2013/06/25/ssl-intercepted-today-decrypted-tomorrow.html SSL intercepted today, decrypted tomorrow] | *[http://news.netcraft.com/archives/2013/06/25/ssl-intercepted-today-decrypted-tomorrow.html SSL intercepted today, decrypted tomorrow] | ||
Revision as of 19:22, 4 August 2013
| Secure Sockets Layer Organic Design procedure |
First we need to ensure that we have a valid SSL certificate for each domain that will be using SSL connections. First generate a self signed certificate for each domain. Remember that this will raise the "untrusted secure site" error in the client browser, for sites that require a proper commercial certificate, use the generate a certificate request for a commercial Certificate Authority procedure instead.
Our convention is to keep all the certificates in /var/www/ssl, so first change the current directory to that and create the certificate with the following command format. Ensure the common name (cn) is entered as a wildcard such as *.foo.com so that the certificate applies to all the sub-domains such as www.foo.com or webmail.foo.com etc. This certificate format will work for both Apache and Nginx.
First we need to create a private key. Note that this process will require a pass-phrase for the key - don't worry, we'll remove it later to make things easier,
Now we need to create a CSR (Certificate Signing Request):
Now we need to remove the pass-phrase otherwise it'll prevent the web-server from restarting without it being entered (you'll need to enter the pass-phrase to remove it though),
Now we can generate the actual certificate:
Each secure domain will require virtual-host definition in a separate file in the /var/www/ssl directory and having the same file name as the domain name it applies to, and can then be referred to by the relevant host container in the web server configuration, for example:
Check the config before restarting with apachectl -t or nginx -t, and if everything is fine, start or restart the web server from /etc/init.d as usual. After starting, follow the web server error log as you start the server and as you make SSL requests and see if problems show up.
Selecting a good set of ciphers
With revelations about mass surveillance in the news everywhere, such as this article, an obscure feature of SSL/TLS called perfect forward secrecy has suddenly become a very important feature to enable.
You'll need at least OpenSSL version 1.0 and Apache version 2.3.3 (or Nginx which has supported it for quite some time now). First check that your version of OpenSSL supports elliptic curve Diffie-Hellman protocols.
If you have support for it, you'll get a long list of output like the following example, or if not you'll get an "Error in cipher list: result.
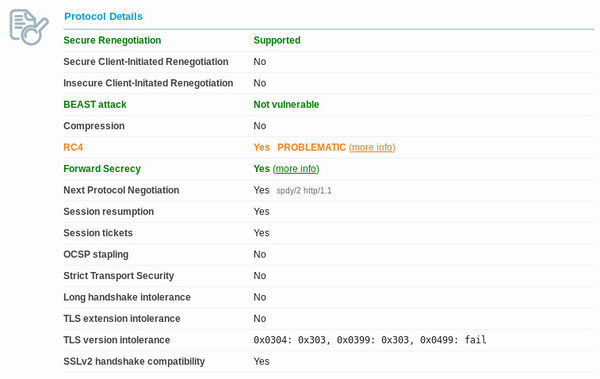
You can then set the protocols in your cypher suite to an optimal list and prioritisation. You can use Qualys SSL labs test. I'm not sure if it's possible to get a combination of ciphers that satisfy everything. The best I've come up with is a value that allows perfect forward secrecy and mitigates the BEAST attack, but it allows RC4 which vulnerabilities have been found in, but haven't yet been exploited in any way. Here's a screenshot of the best result I've managed to obtain (and the best I've seen from the top results in their chart).
The cipher suite settings I found to obtain this result was as follows. It's put in the SSLCipherSuite setting in /etc/apache2/mods-available/ssl.conf, or in the ssl_ciphers value in the site's SSL server container of the NGiNX configuration.