Difference between revisions of "Configure OpenVPN"
m |
m |
||
| Line 1: | Line 1: | ||
We use a VPN so that we can be sure our local browsing traffic's private even when we're on an insecure connection like a hotel or airport. Of course there are many solutions available such as ''ProtonVPN'', ''Mozilla VPN'' or ''RiseupVPN'', but we like to be independent for our security, and also this allows us to customise the ports and locations and have higher bandwidth than a shared solution. | We use a VPN so that we can be sure our local browsing traffic's private even when we're on an insecure connection like a hotel or airport. Of course there are many solutions available such as ''ProtonVPN'', ''Mozilla VPN'' or ''RiseupVPN'', but we like to be independent for our security, and also this allows us to customise the ports and locations and have higher bandwidth than a shared solution. | ||
| − | We currently use ''OpenVPN'' | + | We currently use ''OpenVPN'' for our VPN server software. One big advantage of ''OpenVPN'' is that it has a method of generating client ''.ovpn'' files which most VPN client software supports making it very easy for end users to connect with. In fact the Gnome desktop network manager has optional support for configuring VPNs directly from the desktop that expects a ''.ovpn'' configuration file allowing clients to access an ''OpenVPN'' server in literally seconds, and to then simply switch it on or off any time they like from the comfort of their desktop. |
| + | |||
| + | We may at some point change over to [[Configure WireGuard VPN|WireGuard]] because it's much more modern and efficient. But currently it is much more difficult for users to get up and running which is why we're sticking to ''OpenVPN'' for now. It looks like it won't be long before the Linux kernel and Network Manager will [https://blogs.gnome.org/thaller/2019/03/15/wireguard-in-networkmanager/ support WireGuard] making at as simple to use from the user's perspective as ''OpenVPN'' at which point we'll likely change over. | ||
''OpenVPN'' involves a pretty long installation procedure, but there are some good helper scripts around such as [https://github.com/angristan/openvpn-install Angristan's OpenVPN-install script]. Big thanks to Angristan for this, because it really does make a super complicated procedure unbelievably painless! | ''OpenVPN'' involves a pretty long installation procedure, but there are some good helper scripts around such as [https://github.com/angristan/openvpn-install Angristan's OpenVPN-install script]. Big thanks to Angristan for this, because it really does make a super complicated procedure unbelievably painless! | ||
Revision as of 15:36, 24 March 2022
We use a VPN so that we can be sure our local browsing traffic's private even when we're on an insecure connection like a hotel or airport. Of course there are many solutions available such as ProtonVPN, Mozilla VPN or RiseupVPN, but we like to be independent for our security, and also this allows us to customise the ports and locations and have higher bandwidth than a shared solution.
We currently use OpenVPN for our VPN server software. One big advantage of OpenVPN is that it has a method of generating client .ovpn files which most VPN client software supports making it very easy for end users to connect with. In fact the Gnome desktop network manager has optional support for configuring VPNs directly from the desktop that expects a .ovpn configuration file allowing clients to access an OpenVPN server in literally seconds, and to then simply switch it on or off any time they like from the comfort of their desktop.
We may at some point change over to WireGuard because it's much more modern and efficient. But currently it is much more difficult for users to get up and running which is why we're sticking to OpenVPN for now. It looks like it won't be long before the Linux kernel and Network Manager will support WireGuard making at as simple to use from the user's perspective as OpenVPN at which point we'll likely change over.
OpenVPN involves a pretty long installation procedure, but there are some good helper scripts around such as Angristan's OpenVPN-install script. Big thanks to Angristan for this, because it really does make a super complicated procedure unbelievably painless!
Setting up the server
Simply download and run Angristan's installer script!
wget https://raw.githubusercontent.com/angristan/openvpn-install/master/openvpn-install.sh
chmod +x openvpn-install.sh
./openvpn-install.shStick with the defaults for everything, except in our case we use local Unbound for our chosen DNS server. It really is as simple as that, after the script finished OpenVPN will be running, and you'll be given the location of an .ovpn file that includes all the information necessary for a client to connect to your VPN server.
Setting up Linux clients
On Linux machines running the Gnome desktop, installation is very simple, but we do need to first install some necessary packages.
sudo apt-get install openvpn network-manager-openvpn network-manager-openvpn-gnome
sudo service networking restart
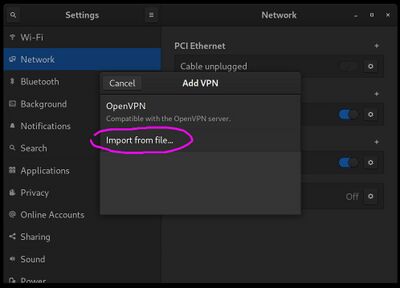
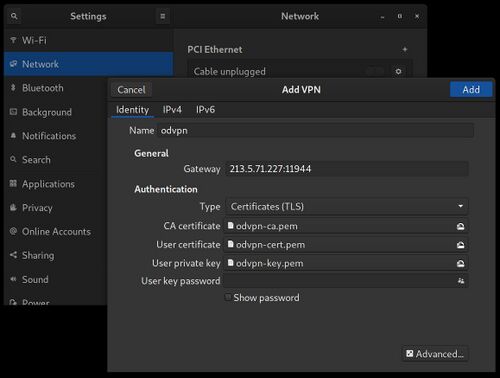
After these are installed and the network is restarted, you can go to the usual network settings applet, click the "+" to the right of the VPN section, and then select "import from file". You will then see the VPN form open with the gateway and certificates already filled out. Click "Add" and then you'll see your VPN in the list where it can be simply switched on or off at any time.
After turning on the VPN, you can go to whatsmyip.org and iplocation.net in your browser to ensure that it's working as expected.
See also
- Configure WireGuard VPN - WireGuard is a more modern and efficient VPN solution
- Angristan's Open VPN installer script
- Installing OpenVPN on Debian 11 using Angristan's script
- Digital Ocean's OpenVPN setup procedure