Proof of agreement
This article will cover a simple method using freely available tools for people to create an agreement amongst themselves which is digitally signed by all participants. The agreement is created in such as way that the identity of all participants, the authenticity of their signatures, and the time the agreement was signed can be verified by anyone. These verifications are very strong, but don't rely on any third-party authority and can be carried out by anyone using freely available tools without any specialised skills or knowledge.
Contents
Public key cryptography
Public key cryptography is the kind of system where the owner holds a secret private key that gives them ownership over the resource the key is protecting, and an associated public key which is safe to share publicly. Two popular example are PGP keys and Bitcoin addresses.
With PGP key pairs, anyone can use a public key to encrypt information knowing that only the person holding the private half of that key will be able to decrypt it. Also, the holder of the private key can sign messages resulting in a digital signature than anyone can verify using the public key. When someone sends a message they can sign it with their PGP key so that the recipient can use the sender's public key to ensure that the message was really sent by the holder of the private key.
In the case of Bitcoin, anyone can send money to any public bitcoin address, knowing that only the holder of the associated private key will be able to spend that money. As with PHP, the holder of the private key is also able to sign messages with it, and anyone can verify that the signature is valid using the public key.
Publicly identifying yourself with a key
The first part to being able to create verifiable agreements between people, is being able to verify an irrefutable connection between a physical person and a public key they hold.
If you haven't already done so, you can publish any of your public keys either on your own site, or on a site that supports various forms of keys in user's profile information such as Keybase, OneName or some of the social networks such as Mastodon. For the purpose of creating a good agreement, it's a good idea to use a recognisable profile picture and include other details such as web site and email addresses in your profile.
This information may be solid at the time the agreement was made, but we want to make an agreement that can stand the test of time. The profile page you've chosen to use for the agreement may not be very permanent, for example the domain could expire, the company running the site go bankrupt or you may decide to delete your account and move to another platform.
A very useful tool to help us with this problem is the "Wayback Machine" at web.archive.org. This site has snapshots of billions of web pages at specific times to preserve the history of the web. And if by chance your profile does not exist in the Wayback Machine when you search for it, you will be given the option of adding it right then.
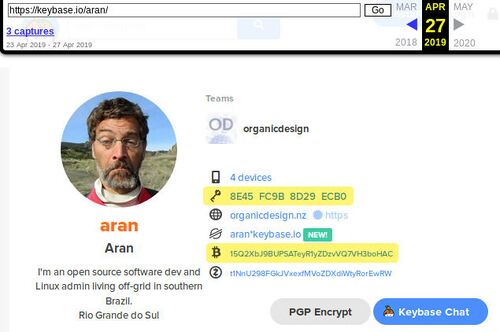
Here is a concrete example. I have a profile in a platform called KeyBase - or at least I did have at the time I wrote this! There were a few snapshots of my profile page already in the Wayback Machine when I checked just now, which you can see in the picture to the right, or by going there yourself.
This is a frozen snapshot of time, no matter what happens with Keybase in the future or what happens to my specific Keybase account, this snapshot will continue to exist in the Internet Archive. You can see that this profile relates a number of things together; it has my name (full name would be better for this purpose) and photo, some of my web addresses and two public keys (highlighted). For most people there would also be provable connections with Facebook and Twitter etc, but I have deleted all such accounts out of my life!
So what we have here is a very strong connection between myself and two public keys that I control, a PGP key and a Bitcoin address. Either of these keys could be used for the rest of the process which involves creating and signing the text of the agreement and using a blockchain to freeze a copy of these signatures in time.
Creating the agreement text
The agreement itself is something that only the participants can figure out, once they've arrived together at a definite statement that they all believe clearly describes what they're all in agreement on that's the first step in creating the text. For my example there will just be a single participant, myself, but of course in reality there could be a number of participants and the text may be many pages.
Aran agrees to buy a pizza for his wife if Bitcoin does not reach a new all time high in 2019.But now we need to list all the participants that will be signing the agreement along with the profile snapshot that you know exists in archive.org (you don't need to specify the archive.org URL in the agreement text, but it's important to know that a recent snapshot of it exists at the time the agreement is created). Another important addition is to include the time, and the current Bitcoin block along with its hash - by including the block's hash, we're providing irrefutable proof that the agreement was not made before this block as created, because the block hash cannot possibly have been known in advance.
Our updated agreement has now been edited so that the identities of the participants includes their profile URL, and the time and block information is appended to the end.
Aran (keybase.io/aran) agrees to buy a pizza for his wife if Bitcoin does not reach a new all time high in 2019.
This agreement was create at 00:10, 2019-08-04 UTC, the Bitcoin block number was 588492 with a hash of
0000000000000000000da391191dd04feefc62299cdfd89ca77c662836da422fGetting the hash (fingerprint) of the agreement
The next step is to get the hash of the agreement, which is a unique fingerprint that matches the exact agreement text. Remember that from this point on the agreement text cannot be changed, even if you see a typo or problem, otherwise the entire rest of the process will need to be repeated again. We'll use SHA-256 hashes because those are currently the most popular throughout the crypto world. You can do this using an online tool such as this one where you can simply drop the file on the page to get the hash, or if you're using Linux or Mac you can do it on the command line as follows (you'll need to know the path and filename of your agreement document).
sha256sum /path/to/document.pdfIn my case the SHA-256 hash of my agreement is:
0f04a514cb059cebef13ec55f8fbe1ef2312d9c757314c25af4ab897e15ef9f3