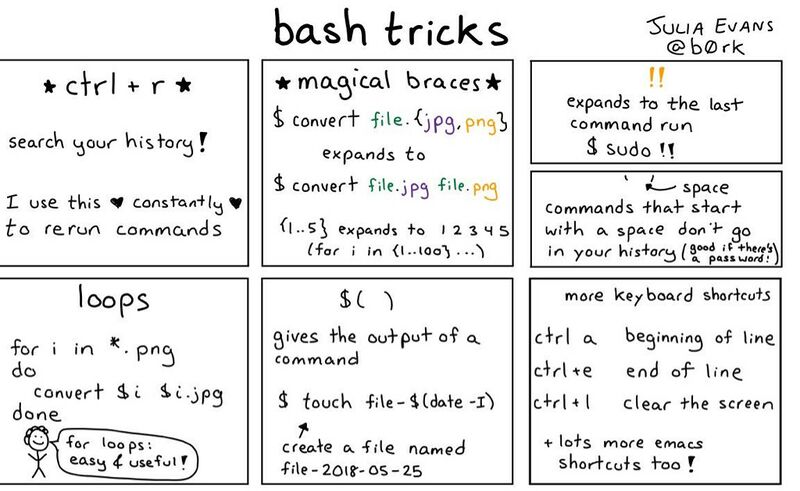
Linux commands
Contents
- 1 Debian package management
- 2 SSH & SCP
- 3 Files & Devices
- 3.1 Clear the contents of a file
- 3.2 List all the storage devices and partitions attached to the system (even if they're unformatted or unmounted)
- 3.3 Get the size of a directory and its contents
- 3.4 Search for file content recursively
- 3.5 Search for file content recursively and tar
- 3.6 Search for file by name recursively
- 3.7 Count occurrences of a word in a file or files
- 3.8 Count the number of lines in a file or output
- 3.9 Search and replace content in files
- 3.10 Copy just the symlinks from one dir to another
- 3.11 Search for files that contain the windows BOM character ()
- 3.12 Mass renaming
- 3.13 Compare two directory structures for differences
- 3.14 Mount a .iso and .img files
- 3.15 Mount a USB stick
- 3.16 Mount a LUKS encrypted device
- 3.17 Clone a device
- 3.18 Changing device UUIDs
- 3.19 Updating device partition tables without rebooting
- 3.20 Downloading from google drive in shell
- 4 Processes
- 5 Image manipulation
- 6 Audio & Video
- 7 System monitoring & management
- 8 Network commands
- 8.1 Restart the network after changing configuration
- 8.2 List all the listening sockets and their ports and programs
- 8.3 Get current default gateway
- 8.4 DHCP
- 8.5 Scan a local subnet for active IP addresses
- 8.6 Get the MAC address and hostname of an IP on the current subnet
- 8.7 Display traffic passing through a port
- 8.8 Make the system prefer IPv4 connections
- 8.9 Test which IPv6 address is being used for public connections
- 9 Internet
- 10 Port forwarding
- 11 General
- 12 Specific guides
- 13 See also
Debian package management
The package management system used on Debian and the "downstream" distros based on it such as Ubuntu and Mint.
Searching for an installed package
Use dpkg and grep;
dpkg -l | grep javawill list all installed packages and filter to only those with "java" in the name
Searching for installable packages
apt-cache performs a variety of operations on APT´s package cache
apt-cache search javalists all packages in the cache with java in the name that are installable
SSH & SCP
See also SSH for more specific uses.
Screen
Screen is an essential utility to use during an SSH session over dodgy connections that can drop or when doing something mission-critical. Just use the screen command without any parameters and another shell session will start (if you exit you'll be back in the original shell session again). This new shell session will remain active even if the connection drops. To get back into the session again later, use screen -R. There are many other options for using multiple screen sessions and multiple windows onto a single session etc, see this screen cheatsheet for more details.
Note: One annoying issue with screen is that the normal scroll-back doesn't work, but you can user CTRL+A then ESC to activate "copy mode" which then allows you to scroll back using the cursor keys or page up/down. To exit "copy mode" use ESC again.
Basic SCP syntax
Example of sending a file to a remote server:
scp -P 2222 /my/local/file.txt USER@example.com:/home/USERExample of retrieving a file from a remote server:
scp -P 2222 USER@example.com:/home/USER/file.txt ./Note using port forwarding for commonly accessed sites you can define non standard ports in your .ssh/config so you never
need to explicitly state them above.
Recovering from an interrupted transfer
This ability is included natively in Linux and used to be very useful for splitting large backups up so they could fit onto small media such as floppy disks. But there's one time when it's very useful nowadays too which is when a large file transfer gets interupted and there's no option for continuation such as when using SCP.
When this happens, go onto the target machine, check how many bytes were transferred of the target file and rename it to "xaa". Then on the local machine, do the following command to split the source file into two parts, the first being of the size of the number of bytes that have already been transferred (in this example 1234567 bytes).
split -b 1234567 foo.tar.gzThe resulting files are called "xaa" and "xab", and the latter is the containing the remaining content that needs to be transferred to the target server. Once you've transferred it across, you can then join the two files (remember you renamed the first part to "xaa" so there's no need to transfer that) together using cat as follows, and then remove all the xa* files from noth source and target servers.
cat xa* > foo.tar.gzTar pipes
## From a local to remote machine
tar -zcvf - directory | ssh remote 'cd somewhere; tar -zxvf -'
## From remote machine to local machine
ssh remote 'cd somewhere; tar -zcvf - directory' | tar -zxf -
## remote tar and pipe to tgz
ssh remote 'cd somewhere; tar -zcf - directory' | cat - > directory.tar.gzPort-forwarding with SSH
SSH allows you to forward ports on one machine to another using the SSH pipes.
For example, using a local port-forward, you could create a local connection into a remote SQL server that's not available to external connections if you have SSH access to machine with running the SQL server:
ssh -nNTL 3333:localhost:3306 USER@SERVERNow you can access the database locally on port 3333.
Or in the opposite direction you can use a remote port-forward you could give SSH access to a machine that's behind a firewall or router by putting its SSH port onto a remote machine:
ssh -nNTR 2222:localhost:22 USER@SERVERYou can now ssh into the local machine from within the remote server on port 2222 instead.
Note that by default the forwarded port is only accessible locally, but you can change this behaviour with the GatewayPorts SSH option.
Lets say you're doing some maintenance on your site and you'd like to redirect all the requests on port 80 to another web-server (SERVER) on port 8080. You could set up your temporary web-server on 8080 on a remote server and then after you've stopped the local web-server, forward all requests for port 80 to 8080 on the remote machine with a local port-forward. By using the GatewayPorts option, the forwarded port 80 is available externally.
ssh -nNTL 80:SERVER:8080 -o GatewayPorts=yes USER@SERVERThis option can be useful for remote forwards too, for example what if we wanted our machine behind the firewall that we want accessible via SSH to be accessible externally? In this case we need to set the GatewayPorts option in sshd_config because it applies to the remote machine, not to the one running the command. If it's set to yes then the forwarded ports will be available externally as well, or you can set it to clientspecified to restrict the access to an external IP defined in the command:
ssh -nNTR 1.2.3.4:2222:localhost:22 USER@SERVERNow the host at 1.2.3.4 is able to SSH into our firewalled machine on port 2222 of USER@SERVER. See also this post regarding security for port-forwarding accounts.
Browsing the net through a remote server with SSH
Sometimes you need to browse using an IP address that's in another location, for example if the content you want to access is only available to local users or if you're buying something and the prices are based on the buyers location. If you have access to a server in the required location, or someone you know in that location is willing to temporarily set up an SSH server that you can access, the you can use the following syntax to set up a local port that your browser can use as a proxy server.
ssh -fnNTCD 1080 USER@SERVER- The f option means to Fork off into the background after successful connection
- The nNT options mean to use this SSH session only for tunnelling, prevent reading STDIN, no pseudo terminal and not to use open up a shell session.
- The C option means to compress the data in the tunnel which is a good idea if you're on a slow connection
- The D option is the main one that tells SSH to set up a tunnel connected to a local port with the port number specified
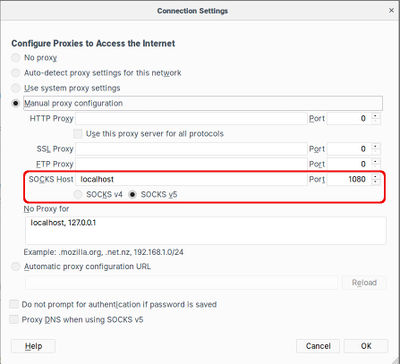
Next you need to configure your browser to connect via this local port. Chromium allows you to specify the proxy details as a command-line option, so there's no need to change the network configuration and then change it back afterwards. Simply open a shell window and use the following syntax (make sure there are no other Chromium windows open when you do this).
chromium --proxy-server="socks5://localhost:1080"In Firefox you need to change the Network Proxy setting in Preferences/General. The changes take effect instantly without needing a restart or anything, but you'll need to remember to change the setting back after the SSH connection is closed.
Files & Devices
Clear the contents of a file
> /path/to/fileList all the storage devices and partitions attached to the system (even if they're unformatted or unmounted)
cat /proc/partitionsTo check what filesystem a device has on it use file, e.g.
file -s /dev/sda1Get the size of a directory and its contents
du -sh /home/foo
Use this more specific version to find the size of a users Maildir folder:
du -sh /home/*/Maildir|sed 's|/home/||'|sed 's|/Maildir||'
Here's another version of du that accounts for dotfiles and sorts the results:
du -sch .[!.]* * | sort -hSearch for file content recursively
Here's an example looking for a phrase within a specific file type recursively through a directory structure, and printing the file names and line numbers of the resulting matches.
grep -rn "Foo" *.phpThere are other tips at stackoverflow.com.
Search for file content recursively and tar
## Find and tar
find . -name "*.R" -print0 | xargs -0 tar -cvf Rfiles.tar
## check contents
tar -tvf Rfiles.tar
## Find and tar.gz
find . -name "*.R" -print0 | xargs -0 tar -zcvf Rfiles.tar.gz
## check contents
tar -ztvf Rfiles.tar.gzSearch for file by name recursively
find . -name "*.R"Count occurrences of a word in a file or files
grep -roh "WORD" file*.txt | wc -Count the number of lines in a file or output
wc -l <FILE>
cat <FILE> grep foo | wc -lSearch and replace content in files
You could also use find and sed, but I find that this little line of perl works nicely.
perl -pi -w -e 's/SEARCH/REPLACE/g;' *.php- -e means execute the following line of code.
- -i means edit in-place
- -w write warnings
- -p loop
EXTS="7z t7z"
Copy just the symlinks from one dir to another
find SOURCE_DIR [-maxdepth 1] -type l -exec cp --no-dereference {} TARGET_DIR \;Search for files that contain the windows BOM character ()
Windows editors often add a BOM character to the beginning of UTF-8 encoded text files, these cause a lot of trouble for many types of scripts such as PHP and the problem can be very hard to track down. This short shell one-liner I found here searches the current directory recursively showing what files have a BOM, you can then use a decent editor like Geany to remove them.
grep -rlI $'\xEF\xBB\xBF' .Mass renaming
mmv is a mass move/copy/renaming tool that uses standard wildcards to perform its functions. According to the manual the “;” wildcard is useful for matching files at any depth in the directory tree (ie it will go below the current directory, recursively).
- Example
The first pattern matches anything with a “.JPG” and renames each file (the “#1” matches the first wildcard) to “.jpg”. Each time you use a \(wildcard) you can use a #x to get that wildcard. Where x is a positive number starting at 1. Copied off: http://tldp.org/LDP/GNU-Linux-Tools-Summary/html/mass-rename.html
Compare two directory structures for differences
This is very handy if you need to know if two directory structures are the same or not including file content. It uses the diff command with the r switch to work recursively and the x switch to allow skipping of the .svn directories.
diff -qrx .svn DIR1 DIR2Mount a .iso and .img files
See this for ISO files and this for IMG files.
Mount a USB stick
If you don't know the device name of the stick, plug it in and find it with the following:
dmesg |grep SCSIThen mount the first partition,
mkdir -p ~/memstick
mount -t vfat -o rw,users /dev/sdX1 ~/memstickMount a LUKS encrypted device
First find the device number for the drive with blkid | grep crypto or df -h or lsblk etc. Then unlock it as follows (note the capital O):
cryptsetup luksOpen /dev/sda2/ luksieThis makes the unlocked content available as a device /dev/mapper/luky, you can then mount this new device:
mkdir /mnt/luksie
mount /dev/mapper/luksie /mnt/luksieClone a device
Remember that this is a very low-level operation and so if you're cloning a live partition you may end up with partially written files or other corruption issues on the destination. Stop as many services as you can first, do an fsck afterwards and manually copy any directories that had issues.
dd if=/dev/sda of=/dev/sdb bs=32MA good way to find more information about the devices first, for example if you have a number of unformatted devices of the same size and need more specific information about the hardware, is to use the 'lsscsi command which gives the following sample output:
[0:0:0:0] disk AMCC 9650SE-2LP DISK 4.10 /dev/sdb
[1:0:0:0] disk ATA Hitachi HUA72201 JP4O /dev/sda
[2:0:0:0] disk ATA TOSHIBA MG03ACA1 FL1A /dev/sdcThe sdb and sdc devices look identical with commands such as lsblk or fdisk -l, but one of the is a RAID pair and the other just a normal drive.
See also: Clone a live partition over SSH
Changing device UUIDs
It may sometimes be useful to change the UUIDs of partitions such as when they've been cloned with a low-level method like dd.
Note: the disk identifier should also be changed which you can do with fdisk from the expert menu.
Check what devices and UUIDs you have in the system:
# blkid
/dev/sda1: UUID="bc459b13-3aad-4017-a68b-ce8ab36275e1" SEC_TYPE="ext2" TYPE="ext3"
/dev/sda2: UUID="86ce60b7-ad4a-44aa-88e2-2aefd5c6c396" TYPE="swap"
/dev/sda3: UUID="b56d82f7-5817-4a52-9763-0b38aa360e2b" TYPE="ext4"
/dev/sdc1: UUID="81d40a02-8019-4c1f-afb8-fb41d117c6d1" TYPE="ext3"
/dev/sdc2: UUID="c57f1400-129a-402a-90f1-820a22c6a2fe" TYPE="swap"
/dev/sdc3: UUID="c23ab65a-c32f-41e3-bd31-51ed563e0099" TYPE="ext4"or:
# ls -l /dev/disk/by-uuid/
total 0
lrwxrwxrwx 1 root root 10 Sep 2 12:10 81d40a02-8019-4c1f-afb8-fb41d117c6d1 -> ../../sdc1
lrwxrwxrwx 1 root root 10 Sep 2 12:10 86ce60b7-ad4a-44aa-88e2-2aefd5c6c396 -> ../../sda2
lrwxrwxrwx 1 root root 10 Sep 2 12:10 b56d82f7-5817-4a52-9763-0b38aa360e2b -> ../../sda3
lrwxrwxrwx 1 root root 10 Sep 2 12:10 bc459b13-3aad-4017-a68b-ce8ab36275e1 -> ../../sda1
lrwxrwxrwx 1 root root 10 Sep 2 12:10 c23ab65a-c32f-41e3-bd31-51ed563e0099 -> ../../sdc3
lrwxrwxrwx 1 root root 10 Sep 2 12:27 c57f1400-129a-402a-90f1-820a22c6a2fe -> ../../sdc2Check what swap partitions you have:
# cat /proc/swaps
Filename Type Size Used Priority
/dev/sda2 partition 3999740 0 -1Create a new UUID and assign it to and ext parition:
# uuidgen
81d40a02-8019-4c1f-afb8-fb41d117c6d1
#tune2fs /dev/sdb1 -U 81d40a02-8019-4c1f-afb8-fb41d117c6d1Do the same for a swap partition:
# uuidgen
86ce60b7-ad4a-44aa-88e2-2aefd5c6c396
# swapoff /dev/sda2
# mkswap -U 86ce60b7-ad4a-44aa-88e2-2aefd5c6c396 /dev/sda2
Setting up swapspace version 1, size = 3999740 KiB
no label, UUID=86ce60b7-ad4a-44aa-88e2-2aefd5c6c396Updating device partition tables without rebooting
- partprobe /dev/sdx
- partx -u /dev/sdx
- echo 1 > /sys/block/sdX/device/rescan
- check partition information before and after with cat /proc/partitions
Downloading from google drive in shell
Thanks to FrankerZ for this! The first command outputs a code which you put into the second command.
wget --save-cookies cookies.txt --keep-session-cookies --no-check-certificate 'https://docs.google.com/uc?export=download&id=FILEID' -O- | sed -rn 's/.*confirm=([0-9A-Za-z_]+).*/Code: \1\n/p'wget --load-cookies cookies.txt 'https://docs.google.com/uc?export=download&confirm=CODE_FROM_ABOVE&id=FILEID' -O FILENAMEProcesses
Kill processes matching a text string:
pkill -f <STRING>Image manipulation
Resizing JPG's and changing quality setting
The first line shows how to reduce and image to 25% and quality to 50% adding "_resized" to the results filename.
convert foo.jpg -resize 25% -quality 75% foo_resized.jpgHere's a Perl script version used to apply this same command to all JPG's (jpg, JPG, jpeg etc) in the current directory.
#!/usr/bin/perl
use File::Glob qw(:globally :nocase);
for (glob "*.jp*g") {
my $img = $_;
s/(....)$/_resized$1/;
qx "convert \'$img\' -resize 25% -quality 75% \'$_\'";
}This command rotates, normalises, greyscales and sets the output quality of set of an image:
convert FILE -normalize -set colorspace Gray -separate -average -resize 50% -rotate "-90" -quality 75% OUT.JPGMaking a PDF from a selection of images
ImageMagick can also be used to make a PDF from many images in a directory:
convert *.jpg -resize 50% -quality 75% -gravity Center -extent 1240x1753 -units pixelsperinch -density 150x150 foo.pdfHere all the jpeg files in the current directory will be resized to half size (in pixels) with a 75% quality setting. Then the page size and print resolution are set (note that the extent parameter is required for gravity to work to ensure the images are centered in the page. The extent is set to the size of the page in inches multiplied by the density setting.
Apply an opaque background of a specified colour to a directory of transparent PNG's
- This command requires ImageMagick to be installed
- It loops through all PNG's in the CWD and puts them in a directory called processed which must exist
perl -e 'qx "convert $_ -background #ff00ff -flatten foo/$_" for glob "*.png"'Audio & Video
ffmpeg (also called avconv on some systems)
Note: Many operating systems including Ubuntu are now using the libav fork of ffmpeg now which means you should use the avconv command instead.
The most common use of the tool is to reduce the size of a video file, the following example makes a video half the pixel size:
ffmpeg -i foo.mp4 -vf "scale=iw/2:ih/2" -c:a copy foo-half.mp4
To concatenate videos (be sure to change the n value to match the number of files you're concatenating):
ffmpeg -i start.mp4 -i finish.mp4 -filter_complex "[0:v][0:a][1:v][1:a]concat=n=2:v=1:a=1[v][a]" -map "[v]" -map "[a]" whole.mp4Here's another variation to also double the volume on the concatenated output:
ffmpeg -i start.mp4 -i finish.mp4 -filter_complex "[0:v][0:a][1:v][1:a]concat=n=2:v=1:a=1[v][a];[a]volume=2.0[aout]" -map "[v]" -map "[aout]" whole.mp4
The following converts a .wav file to an mp3:
ffmpeg -i foo.wav foo.mp3Extract the audio as mp3 from a video:
ffmpeg -i foo.mp4 -acodec libmp3lame foo.mp3Here's a more complicated example which converts mp4 video into mp3 audio at a lower quality with only one channel at 11KHz and 32kbps.
ffmpeg -i foo.mp4 -acodec libmp3lame -ab 16k -ar 11025 -ac 1 foo.mp3To do a whole directory you could do this:
perl -e 'qx "ffmpeg -i $_ $_.mp3" for glob "*.wav"'Or a little more complex; a whole directory with a proper name change accounting for names with spaces in them. This
perl -e 'for (glob "*.mp4") { $i=$_; s/.mp3$/.converted.wav/; qx "ffmpeg -i \"$i\" \"$_\"" }'Use the following commands to extract a small (5 seconds in this example) snippet out of a video (the -ar switch is only needed for outputting to flv I think).
ffmpeg -i "foo.avi" -ss 00:10:10 -t 5 -ar 22050 "foo.flv"See also:
- Simple video streaming with ffserver
- Converting microarray images for bash/imagemagick image file manipulation
- How to install ffmpeg 3.2 in Ubuntu 16
Downloading Youtube from shell
We use yt-dlp now, as the original youtube-dl was shutdown. It can be instanned as a single binary, or using the pip Python package manager, see the main Github project page for instructions. Run it with the -U switch to upgrade it.
Use the tool to download the video, e.g.
youtube-dl URL_OF_VIDEO_OR_PLAYIST
Music only downloading
youtube-dl -x --audio-format mp3 URLUsing a video as desktop background
This can be done with VLC from the command line. There are other ways, but one advantage of using VLC is that it's independent of the window manager or desktop environment. The only requirement is that VLC works.
cvlc --x11-display :2 --video-wallpaper --no-audio /path/to/video/fileThe x11-display parameter is optional and only necessary if you want the video playing on an second screen. Note that the numbers start from 0 and go up sequentially, but the numbering used is based on the physical output, so it could be :2 or :3 even if you only have two screens connected.
You may also need to make some tweaks to your desktop settings, such as the panel.
System monitoring & management
List the top 10 memory consuming processes
ps -auxf | sort -nr -k 4 | head -10
List the top 10 CPU consuming processes
ps -auxf | sort -nr -k 3 | head -10
Limit CPU resources to a process (you may need to first install the cpulimit package):
cpulimit -b -l <PERCENTAGE> -p <PID>
Disable suspend/hibernate
You need to configure the suspend and hibernate actions from the shell in order for it to apply globally even in the desktop login screen. Check the current status with the following, if they're inactive you'll see "target is masked" on all suspend/hibernate types listed.
sudo systemctl status sleep.target suspend.target hibernate.target hybrid-sleep.target
To disable (or mask) them, do the following:
sudo systemctl mask sleep.target suspend.target hibernate.target hybrid-sleep.target
And to re-enable them again,
sudo systemctl unmask sleep.target suspend.target hibernate.target hybrid-sleep.target
Configure login screen
We can configure many of the properties of the login screen in the /etc/systemd/logind.conf file. For example, the lid action is set in the HandleLidSwitch setting which can be set to suspend, poweroff, lock or ignore.
Network commands
Restart the network after changing configuration
/etc/init.d/networking restartList all the listening sockets and their ports and programs
netstat -lpGet current default gateway
netstat -nrThe default gateway is on the last line, it should have the U and G flags set
DHCP
Release current lease:
dhclient -r
Obtain a new lease
dhclient
Query to see if there is a DHCP server and what it responds with:
nmap --script broadcast-dhcp-discover [-e INTERFACE]
Scan a local subnet for active IP addresses
sudo nmap -sP 192.168.1.0/24
Scan the subnet for hosts with a specified port open:
nmap -p 22 --open -Pn 192.168.1.0/24|grep reportGet the MAC address and hostname of an IP on the current subnet
arp -a 192.168.1.1Display traffic passing through a port
This is very useful for debugging interactions with services, for example the following command shows traffic going between a local elasticsearch service and a local client application.
sudo tcpdump port 9200 -qAi loMake the system prefer IPv4 connections
Open /etc/gai.conf and uncomment the following line:
#
# For sites which prefer IPv4 connections change the last line to
#
precedence ::ffff:0:0/96 100Test which IPv6 address is being used for public connections
Servers can be assigned many IPv6 addresses, but which one should you assign to AAAA records pointing at the server? This command shows which address is being used to make outgoing connections which would be the best one to use for incoming connections as well. The address used to test the outgoing connection here is google's public DNS server.
ip r get to 2001:4860:4860::8888- See also: Assigned IPv6 address ranges and IPv6 HOWTO
Internet
Download an url to a local file with continuation
curl -L -O -C - http://www.foo.bar/filewget -c http://www.foo.bar/file
Download a copy of an entire site
This will download an entire site, if the site is already downloaded, then only newer files are transferred.
wget -m http://foo.barPort forwarding
Port forwarding allows a remote client to gain access to a network so an intranet can be accessed.
ssh -fnNTL[PORT]:appserver:[PORT] username@sshdserverThen point your webbrowsers proxy server to appserver:[PORT] and access the intranet etc.
To subvert a firewalled environment where outgoing ssh is allowed.
$ ssh -D 9000 username@remotehostThen point your web browser to a SOCKS proxy @ localhost:9000
Further it's possible to get ssh through a web proxy using corkscrew.
ssh -oProxyCommand='corkscrew local_web_proxy proxy_port %h %p' username@remotehostMonitoring network traffic
You can get daily and monthly traffic statistics that are updated every five minutes by installing the vnstat package. This is very useful if your ISP enforces a traffic limit. You can get reports on individual network interfaces.
Enable monitoring on a specific interface as follows:
vnstat --enable -i eth0And then you can get a report for an interface as follows:
vnstat -i eth0Example output:
monthly
rx | tx | total | avg. rate
------------------------+-------------+-------------+---------------
Nov '17 82.43 MiB | 15.97 MiB | 98.40 MiB | 0.35 kbit/s
------------------------+-------------+-------------+---------------
estimated 91 MiB | 16 MiB | 107 MiB |
daily
rx | tx | total | avg. rate
------------------------+-------------+-------------+---------------
today 82.43 MiB | 15.97 MiB | 98.40 MiB | 10.67 kbit/s
------------------------+-------------+-------------+---------------
estimated 93 MiB | 17 MiB | 110 MiB |Testing UDP connectivity
On the target machine being tested:
nc -ulp PORTAnd on the machine sending the tests:
nc -u SERVER PORTThen type text and hit enter, it should be echoed on the server.
If it's not, check the firewall status and disable:
ufw status
ufw disableGeneral
Add and remove startup items
update-rc.d ITEM defaultsupdate-rc.d -f ITEM removeDate and time
Get the current (or another time specified in --date) time in UNIX timestamp format:
date +%s
date --date='01/30/2012 01:23:45' +%s
Convert a UNIX timestamp into a date/time in the current locale format:
date -d @1282368345Specific guides
- All about fstab
- All about ulimit
- Swap file HOWTO
- Using xargs
- Date format codes
- Setting shell colours
- 59 networking commands and scripts
- Top Linux monitoring commands
- 10 ways to make random passwords from the command line
- Efficient Ways To Read The Log Files In Linux
- Bonding multiple network connections into one - see also this for more detail
- Manually booting from the GRUB prompt
- Digital Ocean tutorial on formatting drives
- Convert an RPM to a DEB with alien
- CPU power & performance adjustment
- Using open with pipes in Perl
See also
- Linux commands cheat sheet
- Ubuntu commands cheat sheet
- Using The Terminal - from Ubuntu help
- Basic Linux Tutorial
- The Debian Administrator's Handbook
- Another excellent cheatsheet site
- bonnie++ - easy to use disk benchmarking tool (good output explanation here)